02/02/2026
$XXX Privilege Escalation Vulnerability Led me to be Application admin
Bug Hunting
بِسْمِ اللَّهِ الرَّحْمَنِ الرَّحِيمِ

Hi Hackers, today we are gonna talk about a basic broken access control vulnerability i have found on a production-based closed project used for calculating the risk measure happens in incidents at medical industries
Overview
the overall idea about it is to create a project to identify the problems faced you in the healthcare facility and the root cause of these problems, then each member in the project will evaluate these problems and rate the impact and its probability of occurrence, it also provide a shared notes between the members
Then the application will collect these evaluation and return the final Risk Management results with some mitigations in a detailed report.
Roles
- Application Admin / Super admin: who manage the users and the whole web application
- Project Manager: The one who create the project and manage the coordinated users and give them permissions
- Coordinator: The one who can evaluate and rate the problems
- Member: The one who can just access the project data without any write permissions.
PoC
The idea of the bug that the application admin can create any user, and the project manager should create coordinator and member users only.
The validation done the server taking the JWT token of the request’s sender, decrypt and extract his role
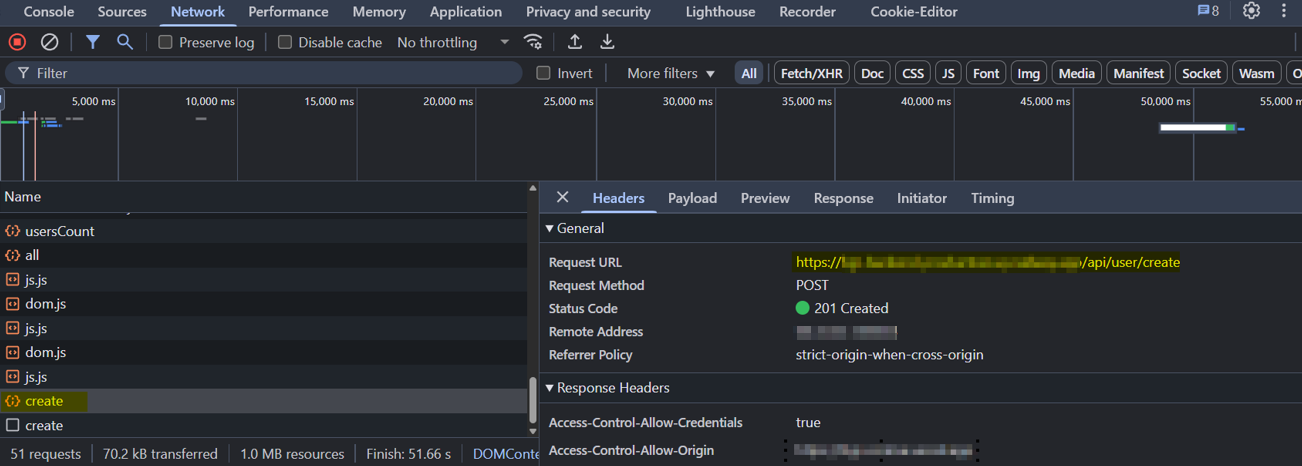
Firstly, I've tried to use this endpoint with lower privilege user like coordinator, and it gave me a 403 Forbidden (Super admin and Project manager only can create users!).
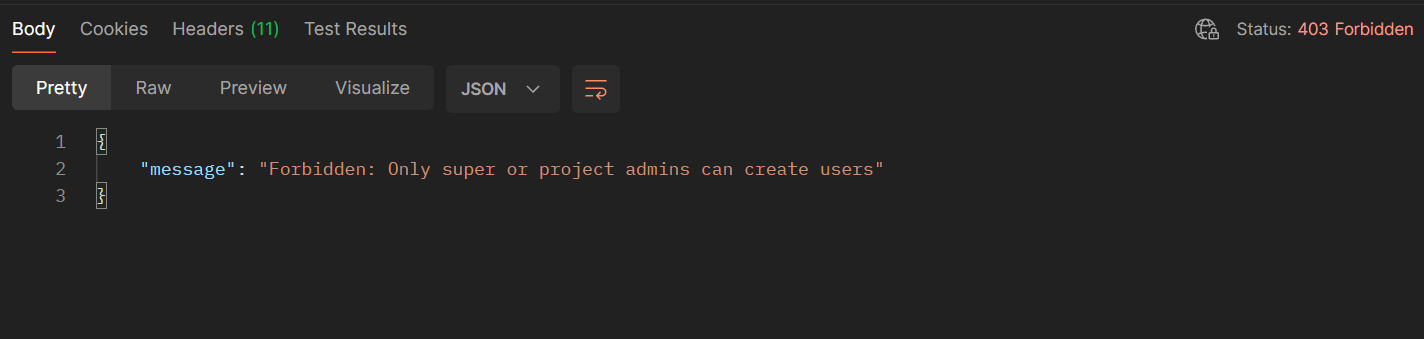
But I've noticed that all of them use the same endpoint!, so it may be a general validation of these two roles
So Secondly, I tried to create a user with project manager privileges but change the new user permissions from coordinator/member to application admin/super admin privilege and it worked!!
So as an image about backend code, the server user only validate on the role of the sender but doesn’t validate if the user can create this account or not.
@app.post("/create")
async def create_user(
authorization: str = Header(None),
payload: Dict[str, Any] = Body(...)
):
if not authorization:
raise HTTPException(status_code=401, detail="Missing Authorization Header")
try:
token = authorization.replace("Bearer ", "")
decoded_token = jwt.decode(token, ENV_SECRET, algorithms=[ALGORITHM])
role = decoded_token.get("role")
if role in ["super_admin", "project_admin"]:
new_user = {
"email": payload.get("email"),
"role": payload.get("role"),
......
}
return {"success": True, "message": "User created successfully"}
raise HTTPException(status_code=403, detail="Forbidden: Only super or project admins can create users")
except jwt.ExpiredSignatureError:
raise HTTPException(status_code=401, detail="Token has expired")
except jwt.InvalidTokenError:
raise HTTPException(status_code=401, detail="Invalid token")
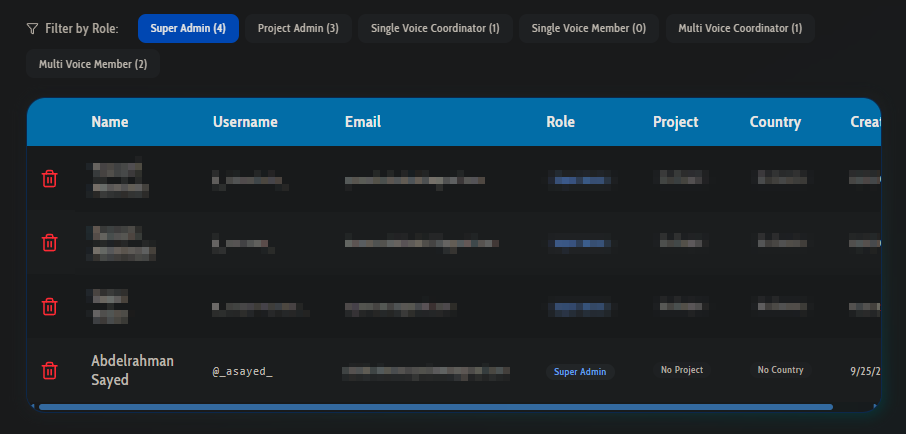
That's it for this writeup, hope you enjoyed it and learned something new. See you in the next one!